“The real trouble with this world of ours is not that it is an unreasonable world, nor even that it is a reasonable one. The commonest kind of trouble is that it is nearly reasonable, but not quite. Life is not an illogicality; yet it is a trap for logicians. It looks just a little more mathematical and regular than it is; its exactitude is obvious, but its inexactitude is hidden; its wildness lies in wait.”
-G.K. Chesterton
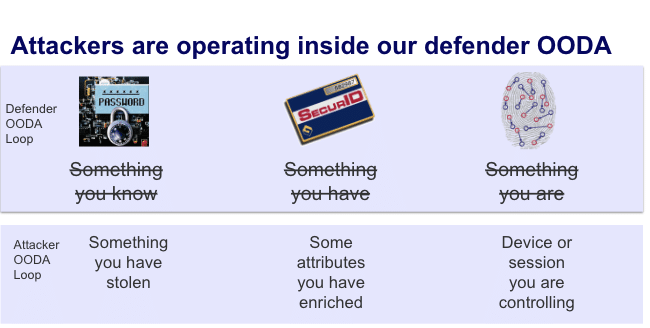
Every security pro knows that authentication is:
- Something you know
- Something you have
- Something you are
This is baked into every single security text, process, policy, and tool. It has served us well. But now, it’s clouding the thinking of security professionals, and limiting our conception of authentication in a way that hands an advantage to our adversaries.
Security is much more than a set of policies and rules. Security is about the coverage and efficacy of controls in the face of adversarial use.
In other words, the efficacy is not determined by the control, but by the adversary. What happens to our controls when threats find a way to operate inside of our identity protocols?
The leading cause of data breaches and security issues has been compromised credentials. These are the very things we rely on for solving security and they are the area most successfully attacked. Moreover, that trend is only intensifying as criminals increasingly leverage GenAI in their attacks; an analysis of Forter’s data shows that ATO attempts increased by 46% between 2023 and mid-2025, largely driven by AI-enhanced phishing and social engineering techniques.
Time has come to refresh our thinking on our most foundational control – authentication.
Look at Authentication from a Threat Perspective
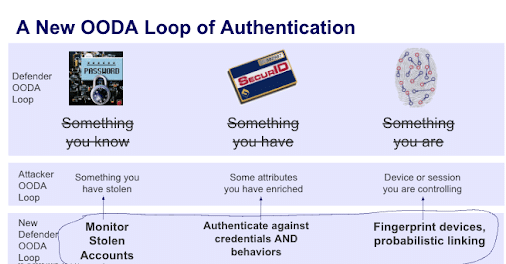
Instead of first pass, high level summaries (like something you know, something you have, and something you are) a much more sober take is to look at authentication from a threat perspective.
For those with stolen credentials, authentication looks quite different. It’s more like:
- Something you’ve stolen
- Some attributes you’ve enriched
- Some device or session you’re controlling
The difference in these two viewpoints is the difference between night and day. And this is the nuance that attackers use to mount the vast majority of successful attacks on the web.
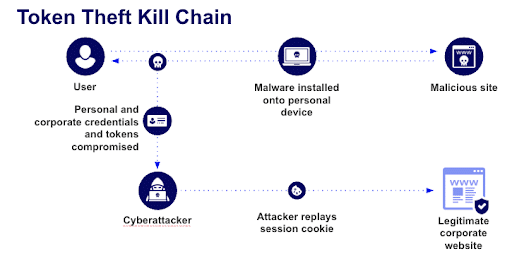
Breaking down the compromised credentials kill chain shows that when what is assumed to be a control is inverted to become a vulnerability, the attacker gains significant leverage. In this case, the user logs in, which grants them a valid session cookie.
However, attackers’ kits have long progressed from simply guessing or stealing passwords. Now, through infostealing malware like Raccooon, Redline Stealer, Vidar, and others, attackers can gain access to the session cookie and replay them to impersonate the legit user. It’s a powerful shift. Forter’s internal data shows that when fraudsters invest in removing red flags from their hack, they get much further in the attack flow before being stopped. Sophistication has increased so much that in some cases, there’s as much as a 100% uptick in incidents in which malicious actors who have managed to hack into an account manage to reach checkout. It’s good to catch them there – but it would be much better to block them earlier.
Effectively, attackers are taking the same access level as the victim, but for malicious use. This example uses a traditional session cookie, but can work with a variety of different session tokens like JWT, Github secrets, AWS tokens, OAuth, and others.
The typical Infosec industry response to authentication weakness is to raise the protection strength. This has led the industry on the following authentication journey:
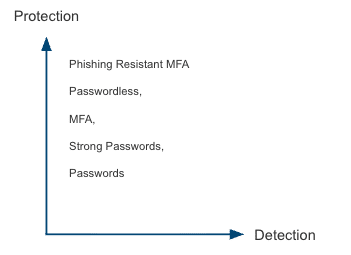
All of these offer incremental improvement, and I am a strong supporter of continuing to increase the strength of authentication. But now that we are multiple decades into this journey, it’s worth asking: Why did the previous strength levels not hold?
I believe the answer is an industry threat model that does not give the attackers enough credit for their ability to evolve and adapt. Phil Venables likes to remind us that “attackers have bosses and budgets, too.” There are simply too many valuable assets behind authentication controls to fully deter adversaries with an incremental strength upgrade. Even when the control works as planned in situ, the attackers will pivot to related capabilities like provisioning and help desk systems.
Think of the Chesterton quote at the start of this piece: attackers’ wildness always lies in wait. You’ve built a rational, reasonable security framework that follows best practices and meets sensibly probable attack types, especially those you’ve seen before. The nature of a malicious actor is to outmaneuver exactly what you’ve just built.
“The Americans would be less dangerous if they had a regular army.”
-British General Frederick Haldimand, Boston, 1776
In 1776, the British army generals assumed if George Washington and the Americans would simply follow the British rules of engagement the fight would be simple. But instead, the Americans pivoted away from meeting a better trained, more experienced, and equipped force in the field. The Americans changed the game to alternative spots where they could fight on their terms, thus turning predictable “show of force” British structures into a weakness.
Detection: The Missing Emphasis of Authentication
As an industry, the investment focus on authentication has almost exclusively gone to moving up the Protection curve. This makes for incremental tactical improvement. But at the same time, when a weak spot is found (either in the control or a related system) it leaves attackers significant room to roam – undetected. For instance the Brickstorm campaign, reported on by the Google Threat Intelligence Group, went undetected in various victim environments for an average of 393 days. That’s an astonishing period of time.
The relative lack of focus on authentication as detection shows that security designers have overindexed on improving protection without realizing that those controls are as susceptible to failure as anything else. Like Richard Bejtlich has said, “all prevention fails eventually.” Access control systems require monitoring. Industry progress has mostly left the detection flank exposed.
Since a control will always fail in the face of a determined, capable adversary, where should we focus next? More protection? There is a better way:
“The main lines of defense, starting from the resource, you truly need something like an anomaly detector, something that observes your requests and makes a determination of whether they are legitimate requests or if they have a chance at being part of an attempt to compromise. Today anyone who operates even a bit of scale on the Internet needs to do this.”
– Vitorrio Bertocci
Example: MFA
Defenders know passwords cannot adequately protect a system. Today, most organizations use or are moving toward MFA.
MFA adds a new speedbump to the attacker’s path. However, digital commerce has more than doubled in value in the last 5 years, reaching more than $4 trillion. It’s predicted to double again in another ~5 years.
Attackers aren’t going to be deterred by MFA. There’s too much valuable data at stake.
In response to the increasing ubiquity of MFA, attackers have shifted from simple methods like password retry and brute force guessing to “MFA bombing,” retry fatigue and attacks targeting adjacent dependencies like source code, help desks and MFA prompts. GenAI has given these attacks a boost of scale and helped to democratize sophistication.
How might defense against this look in practice?
To begin with, let’s give the attacker the credit they deserve. They are goal-driven and their goal is not to break our latest control. It is to exfiltrate data and assets of value. They will pivot until they find their way. This means a broader view of defense like the adapted diamond model below is to consider authentication as much a matter of detection as protection.
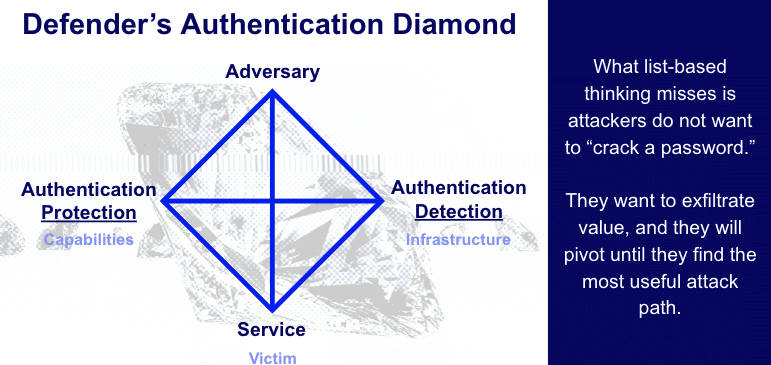
The detection graph should be drawn from as wide a set of attributes as possible, and because identity-based authentication is inherently a behavioral relationship, these attributes have to reflect behavioral monitoring. There is prior work deployed in many companies on fraud/payment layers, but now is the time to move these earlier in the user journey, and to backstop authentication and identity protection with detection using a graph for visibility. It’s also time to start internalizing that protection against fraud, payment vulnerabilities and cybercrime are part of the same big picture.
To defend against an attacker graph, use a defender graph:
- Passwords
- Tokens
- MFA prompts
- Device information
- Behavioral information
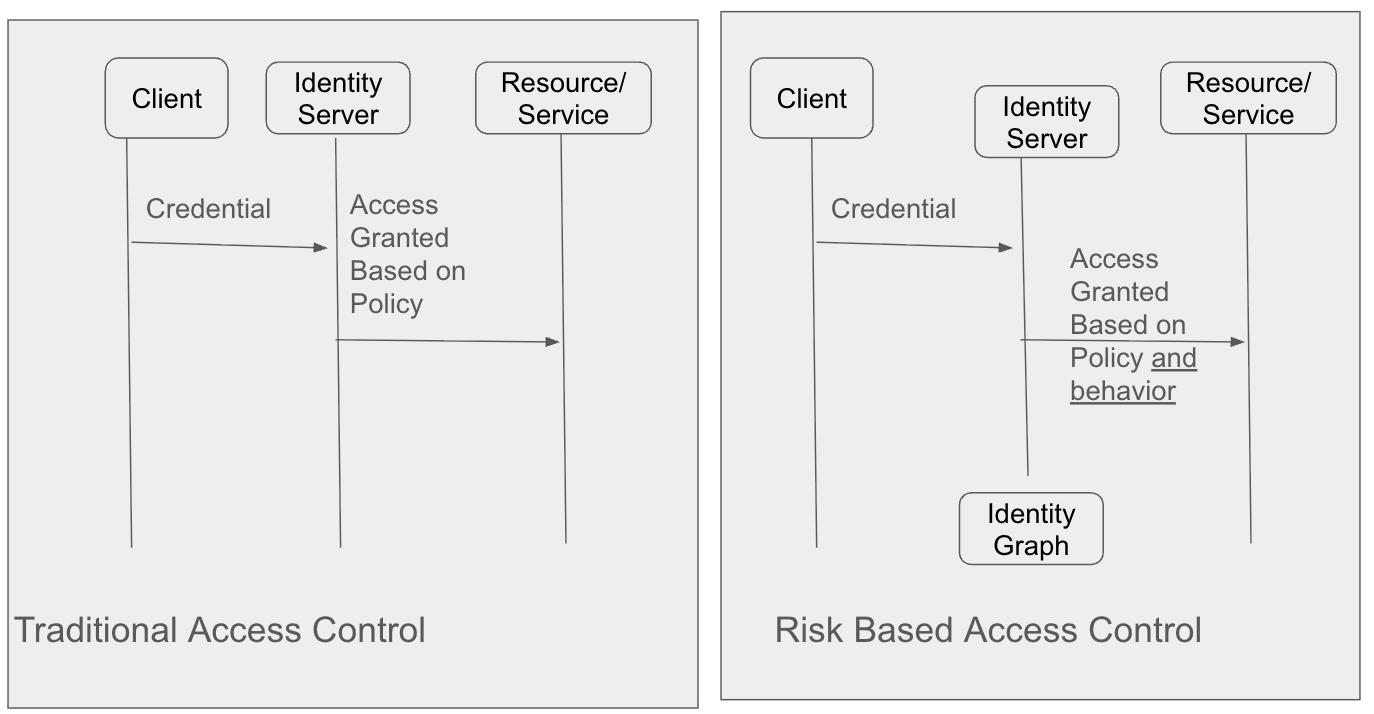
By adding an Identity Graph for detection, defenders can see how an account is accessing a resource. Checking for a valid credential as many consumer IAM systems do is a start, but as we have seen from Infostealer, these are vulnerable to replay, spoofing, and account takeover. To detect these type of threats, defenders should use real-time evaluation of access logs to determine:
- Is the access from a known or trusted device?
- Is the access request associated with the user’s previous actions?
- Is the access behavior similar to other known attacker TTPs?
- Does the access request trip any velocity checks?
- Does the request come from a known network or VPN?
- Does the request come from a bot?
- What type of browser or client does the request come from?
- Is there a device fingerprint that can be used to correlate behavior?
- Is this account behavior similar to past user behavior?
Where does this leave us? We started with a decision loop based on defenders’ goals, then layered on the attacker decision loop. I think our next age of authentication needs to reflect attacker capabilities just as much as it currently tracks our control goals.
This leaves authentication in a radically different and deeper spot, where authentication is continuously informed by detection, not just user inputs and predictable prompts.
Identity Defense principles
Moving beyond the simple view of authentication to something more purpose-built for the current threat environment, think about these principles to augment traditional authentication:
- Ongoing: Detection services should observe all traffic and alert the protection gateway to block a request, terminate a live session or force a reauthentication whenever necessary.
- Layered: Protection always fails eventually, because an attacker isn’t following a script but climbing around until they find what works. Layered protections mean that even when this occurs, the danger can be detected and mitigated.
- Enhanced at every level by detection: Detection isn’t just relevant at login, but should be used to identify bots, suspicious behavioral patterns, ATO TTPs, stolen credentials in use, stolen devices, etc. across the user journey.
Conclusion
Ross Anderson wrote about ATM Fraud in 1993:
“System designers have suffered from a lack of information about how their products fail in practice, as opposed to how they might fail in theory. This lack of feedback has led to a false threat model being accepted. Designers focussed on what could possibly go wrong, rather than on what was likely to”
With account takeovers and compromised credentials running roughshod over systems, we live in a similar world today to Anderson’s ATM tangle. Our organizations sorely need reliable detection systems in place so that authentication systems can learn and adapt based on how they are being used and abused in practice.
Taking practical steps to defend your business in this reality is easier than you think. Below is a sample checklist to think about ways to augment traditional authentication approaches.
Checklist
Practical defense steps
Identity layers
- Reduce identity layer attack surface
- Identity protocol selection
- Identity protocol protection
- Identity protocol detection
- Anomaly monitoring and response
System layers
- Build Open Systems
- Use networks like ISACs
- Study your opponent’s TTPs
- Connected layers from detection to protection and response, informing actions – ideally automated actions
- Tie the detection TO the action
- Avoid patterns that your enemy can predict, alter your behavior
- Learning capabilities – bring in new behaviors, and discard old ones that don’t work