Our latest Security Insights podcast episode, featuring Allison Miller, highlights how cybersecurity and fraud teams can work together to prevent fraud more effectively. And the best way to bring these teams together is by building a fraud fusion center. Rigid rules-based systems cannot deliver effective fraud prevention because the rules themselves are the fraudsters’ target. Today, fraud systems based on rules are a problem, not a solution. But a fraud fusion center brings cybersecurity and fraud teams together to stop fraudsters in their tracks.
Better Together: Fusing fraud and cybersecurity to stop fraudsters from cashing out
One thing defenders can learn from fraudsters is that fraudsters will look across an entire system to identify weak points and combinations to extract cash or value from online accounts and systems. Attackers operate practically and holistically to identify entry points and extract cash and value. Fraudsters are not concerned with whether the insertion or extraction points are technical, process, or operational weak points. They are just concerned with reliability and efficiency.
Similarly, defenders should work across organizational spaces — both fraud and cybersecurity teams and tools to add friction to fraudsters’ attempts. Tools, organizational structure, and culture vary among cybersecurity and fraud teams, and industry leaders often posit building fusion centers as the best way to stop fraudsters in their tracks. Allison describes this as the compounding effect of behavior, looking for layered attacks, especially around profile changes.
“It’s never just a change. It’s the compounding effect of behaviors, before and after,” Allison said. “When I worked in fraud, one of the things that I tried to instill into the work I was doing was ‘think then act.’ Continue collecting information. Something happens. It’s interesting. Keep watching. And then you act when you have enough information and before value moves. That improves the chances that you’re going to get it right, and also helps you learn some things that may help someone else, from a different account from being victimized, for example.”
Whether fraud and cybersecurity teams work together or independently, they need tools to help them identify risky behaviors quickly and can recognize that bad actors all behave differently.
The business value of fraud fusion
Bringing together cybersecurity and fraud teams in a fraud fusion center provides clear value to organizations. Fraud events like account takeovers create a negative customer experience, especially for many of the most valuable customers. Financial loss in both fraud loss and top-line revenue, plus the hassle of unwinding from fraud events, create a harmful stew of events for companies and customers. Account takeover events can occur when ownership of protecting the customer session is divided across departments. The fraud fusion center is positioned to bring a 1+1=3 value from the combination of cybersecurity teams and fraud working hand in hand to defend account security at an identity level. Note that I use the fraud fusion concept throughout this paper not to denote a single physical center or organizational team structure, but rather a center of collaboration across disparate teams.
Leverage the network effect on threat intelligence
The catalyst for Fraud Fusion centers is the network effect. In the same way that Visa, Mastercard, Amex, and Discover networks allow you to stroll into a remote tropical island on vacation and swipe a small piece of plastic to pay for your hotel, the Network effect can also work to a defender’s advantage. Defenders can leverage the network effect’s strength in numbers to identify and separate malice from legitimate customers. The key for defenders is identifying the right trust networks and how to plug into them.
The fact that you see these attackers for the first time does not mean that it is the first time they are attacking an organization like yours. Networked threat intelligence adds a vital level of visibility to detect and block account takeovers in real-time.
Cybersecurity and fraud collaboration
To maximize utility, teams must collaborate on fraud prevention in several ways, especially on operational and technical levels.
Operational and technical collaboration
Creating value in fraud fusion centers means collaboration with fraud and cybersecurity teams. There are several ways to accomplish this. From an operational viewpoint, there are opportunities to coordinate closely in incident and event response to ensure the required data is gathered quickly.
Cybersecurity teams typically have excellent visibility and monitoring of the user session journey from account creation, authentication, authorization, and other events. Cybersecurity teams focus on protecting the user’s journey across their session journey, ensuring authentication and authorization work as expected. Fraud teams meanwhile focus on account takeover and anomalies, such as velocity and abuse.
These different focus areas mean that the tooling, process, and personnel are quite different, but at the same time, fraudsters are not deterred by organizational silos. In fact, they seek them out. The nuanced themes where one department ends and another begins are happy hunting grounds for fraudsters to find and exploit them.
Use Cases for Fusion center opportunity
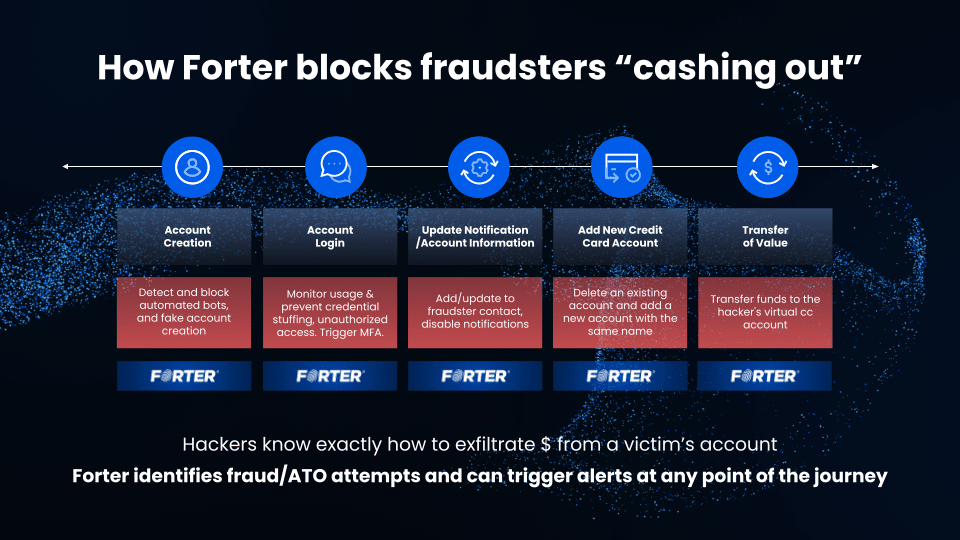
A fraud fusion center allows organizations to align data, technical and operational capabilities to enforce security controls and rigorous fraud detection capabilities across various use cases. Fraudsters increasingly leverage automation via bots and human-assisted automation to attack systems at multiple points:
- Account creation: registering and testing fake and test accounts manually and via bots.
- Login: including credential stuffing via stolen credentials.
- Profile updates: communications routed to fraudster-controlled numbers/emails, disable notifications – may include locking a user out of the account.
- Transfer of value: payments or value moving around or exiting the account.
The main underlying touch point for the use cases listed here is to ensure that at these critical points, threat intelligence and trust networks are used to inform these decisions and make the best decision for the user at each step in the journey.
Preventing fraud requires intelligent solutions
The end goal is for fraud systems to gain as much visibility as is practically useful, moving to omnichannel eventually. The best near-term opportunities are using identity-based visibility and detection that links session visibility which cybersecurity teams can provide with real-time threat intelligence and attacker tactics that fraud systems can deliver. Analytics should be in place to measure success over time. Response systems should be coordinated where events like step-up authentication can be handled and incident response where required.
As fraudsters invest in automation, rules-based systems have become part of the problem. Solutions require not static rules which fraudsters can game, but rather intelligent automation based on real-time trust networks that identify malice, fraud, and abuse across the user session.
Want to learn how teams can work together to fight fraud? You can watch this and other episodes of Security Insights on YouTube!