Fraudsters today are growing more sophisticated than ever before. Instead of launching high volumes of indiscriminate attacks, they focus more on hiding and manipulating their identities to increase their chances of success. For example, fraudsters will often purchase payment and account information of legitimate buyers on the dark web, and attempt to replicate their identities to complete transactions and avoid being caught. As fraudsters continue to get better at this, merchants cannot just rely on basic information like email addresses, IP locations, or device fingerprints to decide if a consumer is trustworthy or not, as these identifiers can easily be changed, manipulated or stolen.
In order to gain the necessary context to understand the person behind each transaction and identify fraudsters, merchants require additional, more sophisticated capabilities:
- Data on the user’s behavior – i.e. which pages they visit, how much time they spend on each page, their clicking patterns, the language of their keyboard, etc.
- The history of the user’s behavior on the site – how does this user’s current behavior compare to how they’ve behaved on the site in the past?
- A global network of merchant data – in order to understand how this person typically behaves across other sites (without sharing confidential information)
- The ability to recognize specific users – even if they log in with a different email, name, etc.
By using and analyzing this depth of data, merchants can then begin to ask themselves the following questions:
- Have we seen this person or pattern of activity before?
- What other identities is this person connected to?
- Is this person who they say they are?
How do we know if we can trust you?
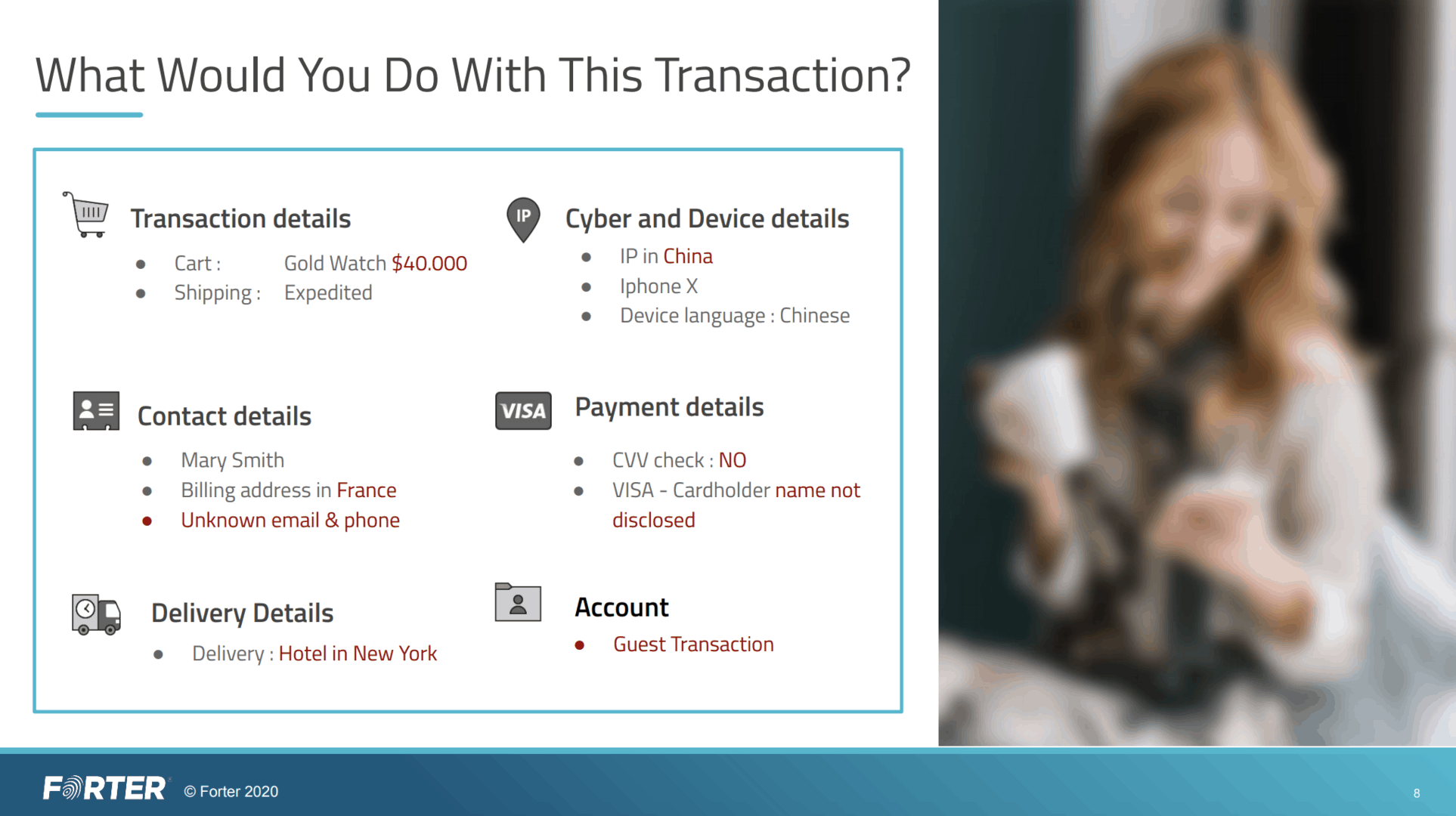
Take, for example, a french woman buying an expensive watch for her husband while in a hotel room in New York City.
While the initial details of this transaction may seem suspicious, immediately declining her would be a mistake. It would result both in the loss of an expensive transaction, and the loss of this customer’s business in the future, as she’d likely be frustrated with the brand for falsely declining her.
If the merchant took a more comprehensive approach, they would soon realize that this buyer is in fact legitimate, and should be approved right away.
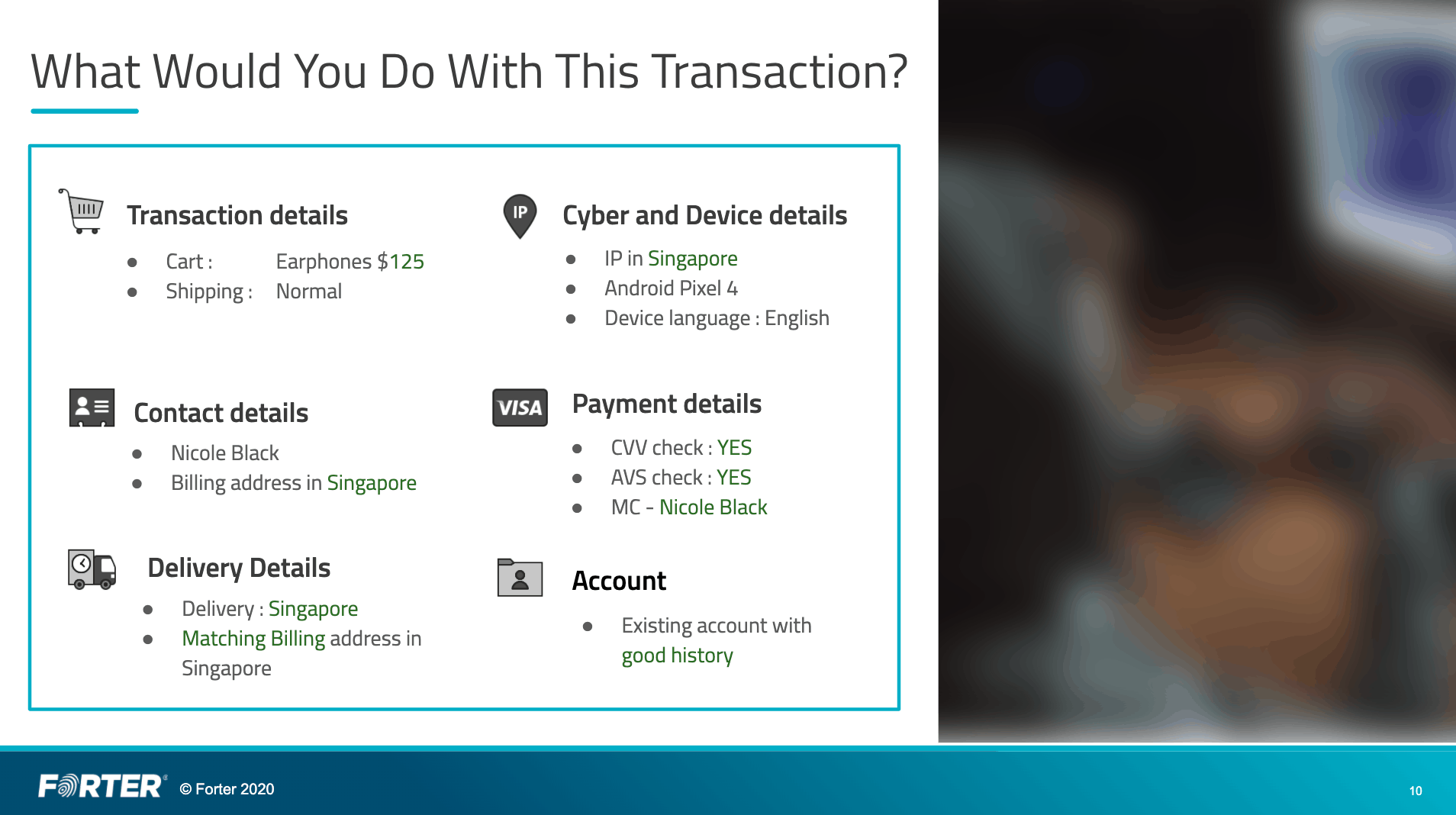
The opposite can also be true. At first glance, a transaction may look like a legitimate consumer with straightforward contact information and payment details.
However, a deeper dive into this user’s behavior and history reveals that a fraudster is using stolen information to hide their identity and complete a fraudulent transaction.
For merchants in today’s e-commerce environment, accurately identifying the person behind each transaction is critical in ensuring that legitimate customers enjoy a seamless shopping experience while fraudsters are blocked before they strike.
To find out how merchants can implement this strategy and make the right decisions to mitigate fraud and avoid turning away good customers, we’ve recorded an on-demand webinar featuring Monica Acree, Forter’s VP of Sales in the APAC region, and Amaury Desrosiers, Forter’s Director of Solutions Consulting. You can download the recording here.